title: “Decrypting HTTPS with Surge” tags:
- Networking Tools slug: c9d4b476 date: 2020-12-30 19:29:25 summary: “How to enable HTTPS decryption (MitM) in Surge on macOS and iOS, why it’s useful, and caveats.”
I wasn’t satisfied that a certain fitness app’s personal health data could only be viewed in the official app. Using Surge, I captured the requests; now I can pull data via Postman or my own scripts/apps.
Benefits of Decryption
Decrypting lets you capture and view request/response payloads. Benefits include:
- Auditing whether a web/app client is sending sensitive data in the background
- Building your own client or admin panels based on the APIs
- Writing scripts for one‑click actions, like checking balances or automating daily check‑ins
Here’s how to enable decryption.
Enable Decryption
- Examples use macOS
v4.0.3and iOSv4.4.3. - Surge has supported decryption since macOS v3 and iOS v3; features and names may differ slightly.
Configure (macOS)
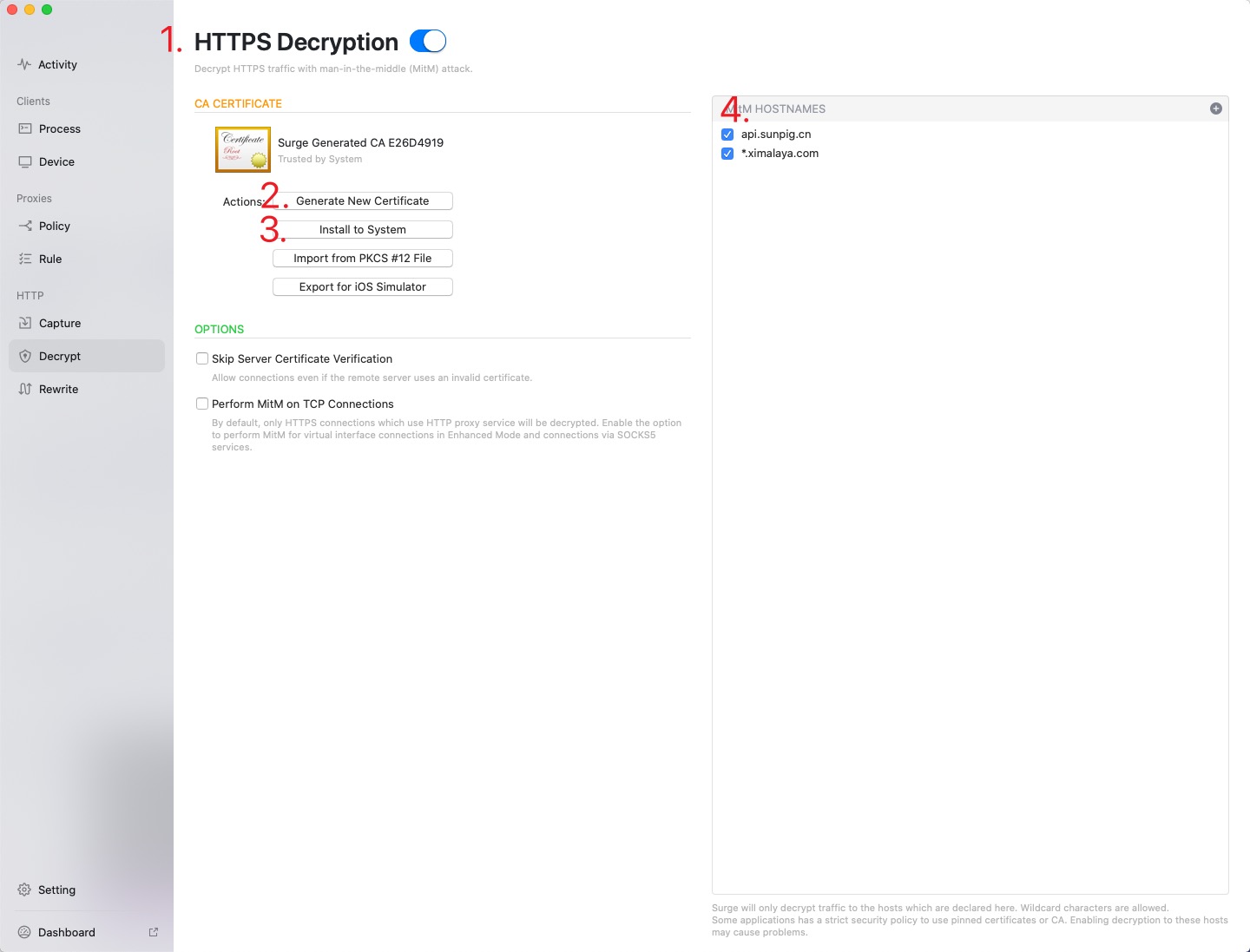
As shown, in order: enable HTTPS decryption → generate certificate → install at the system level → add domains.
Configure (iOS)
iOS is a bit more involved. First set the default browser to Safari (if you only have Safari, ignore this). iOS recognizes the downloaded certificate properly via Safari.
Then follow the steps as illustrated:
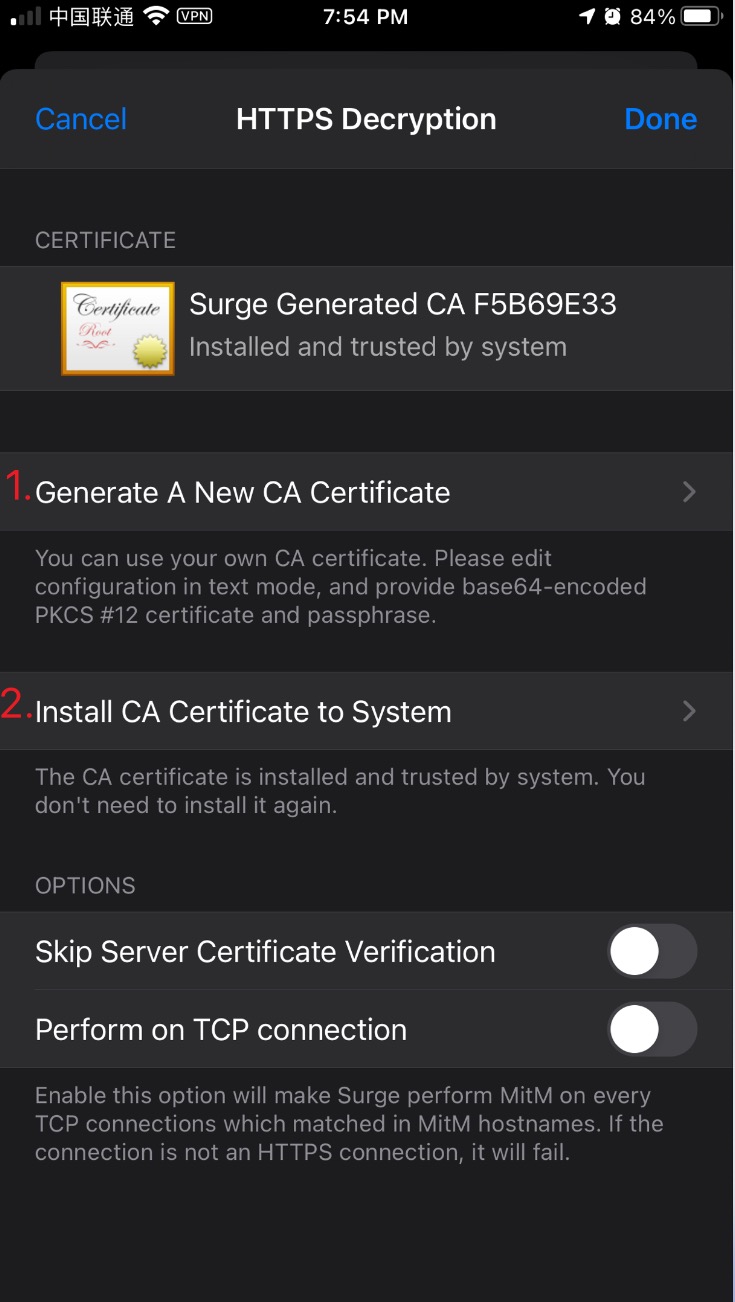
After installation, go to General => About => Certificate Trust Settings and trust the certificate. Surge will indicate trust status when configured correctly.
Finally, enable MitM and add the domains.
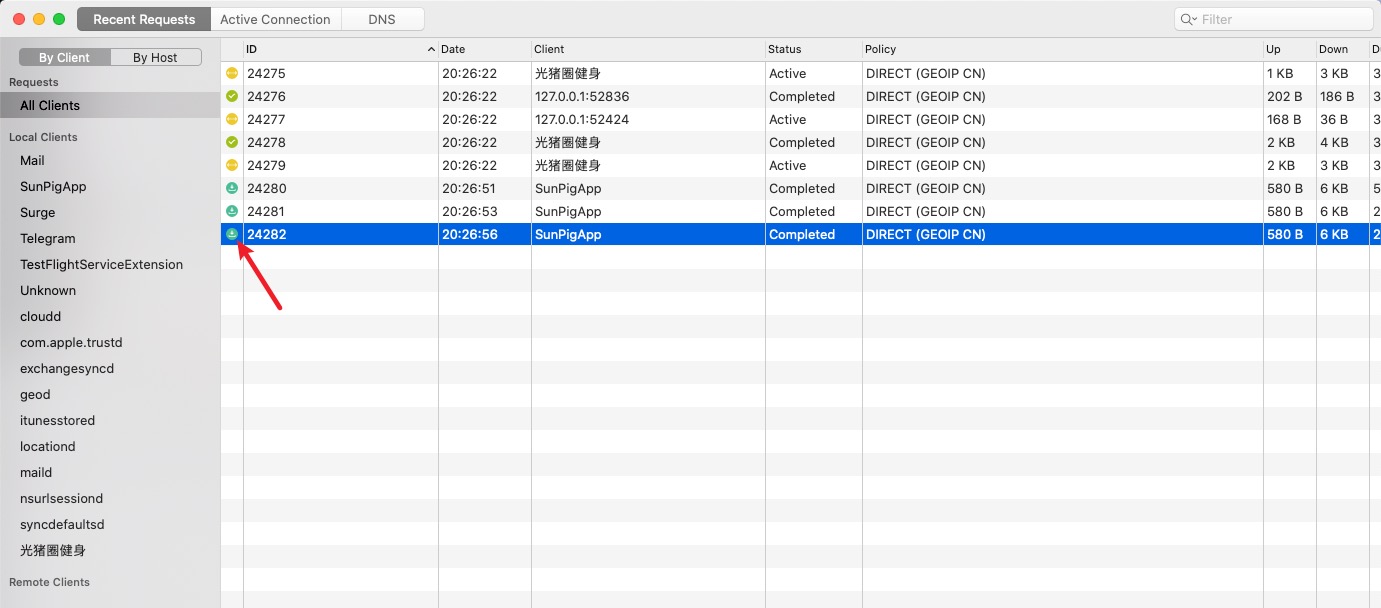
Dashboard
After enabling decryption, view decrypted bodies in Dashboard (macOS) or Utilities => Recent Requests (iOS).
- Demo uses the macOS Dashboard; browsing there is recommended.
- In the Dashboard, enable HTTP Capture; otherwise bodies won’t be decrypted.
- Note the small icon color — on success it looks as shown; if decryption fails you’ll see
MitM failed.
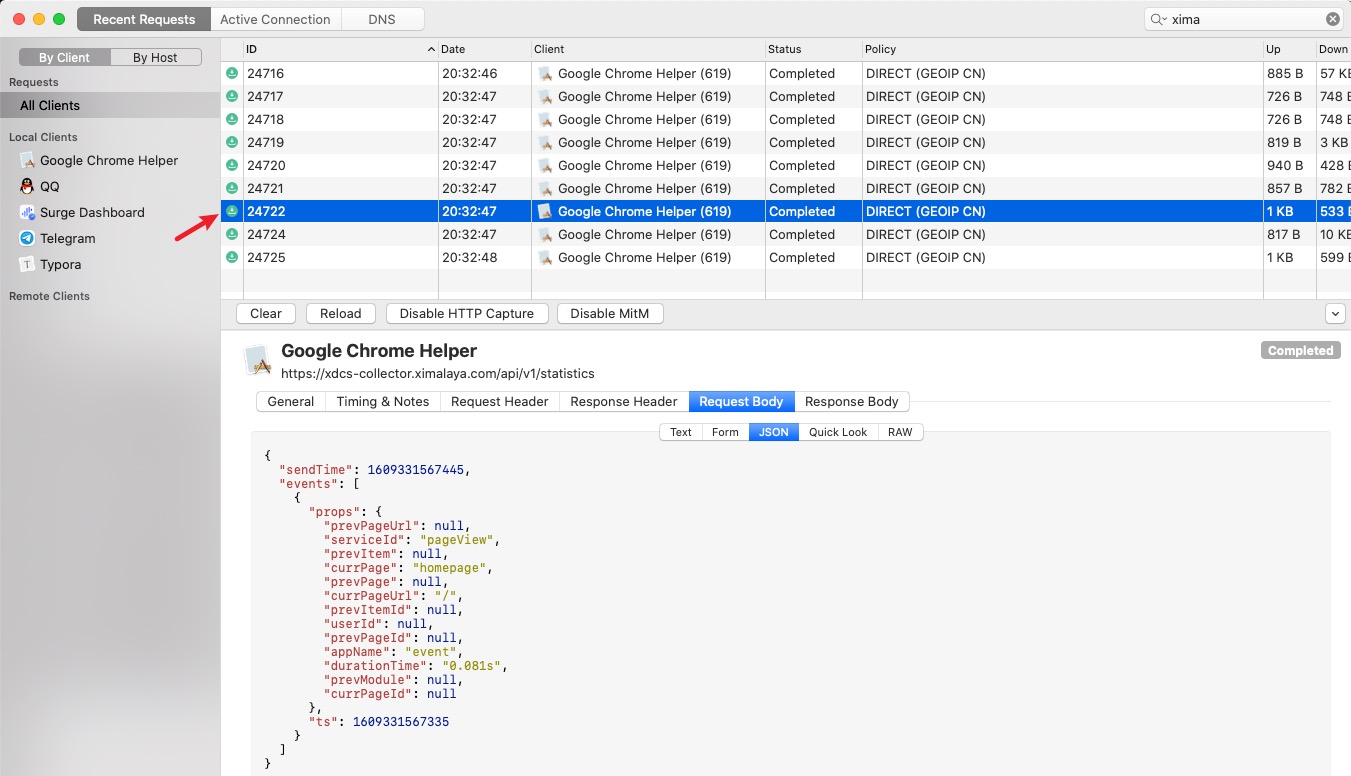
You should now see request and response bodies.
Connect to a Remote Device
Sometimes you want to view iOS capture data from your Mac. Steps:
Enable Remote Controller:
Home => More Settings => Remote Controller
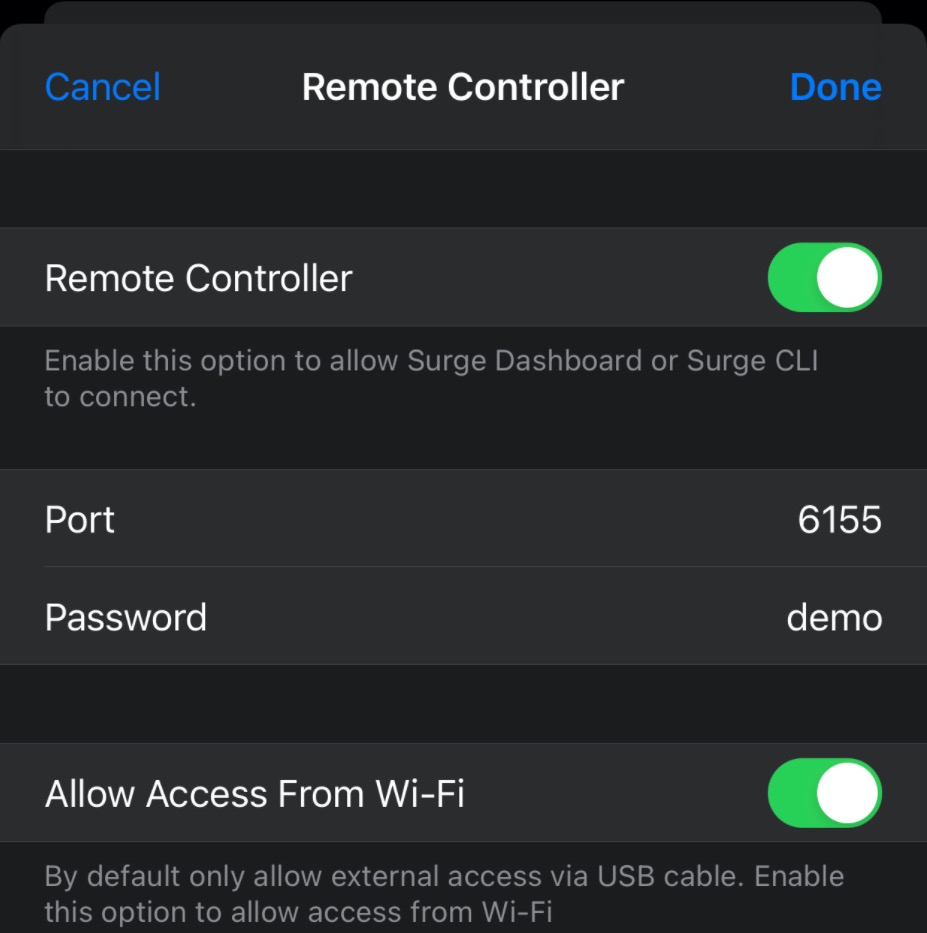
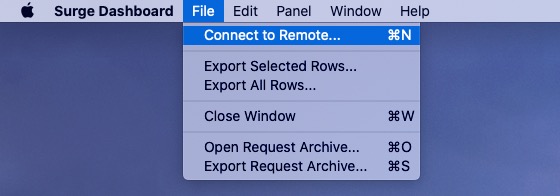
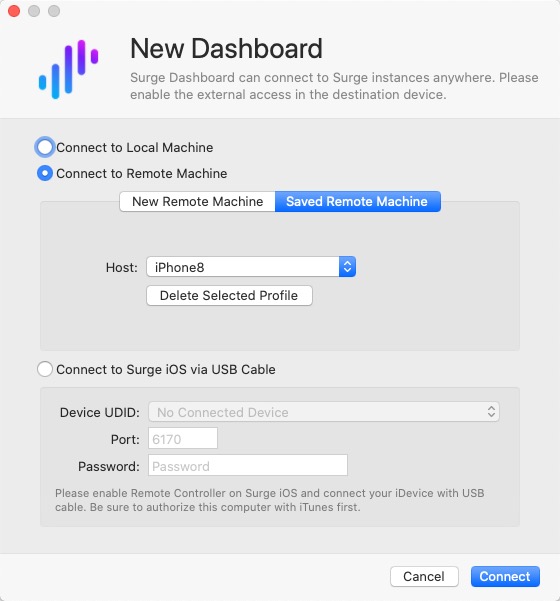
If you see connection refused, verify IP/port/password and retry.
Notes
MitM adds an extra decrypt/encrypt step for requests/responses and may slightly impact performance.
Some apps only trust specific certificates (certificate pinning), so MitM will fail.
Apps with certificate pinning only trust certain certificates or issuers. MitM won’t work in those cases (e.g., iOS requests to apple.com and icloud.com).
The generated certificate is self-signed; if the private key leaks, manually untrust it.
MitM failure is unrelated to performance. It usually means the client closed the connection during the handshake (pinned certs, client logic canceled the request, or you attempted MitM on non‑TLS traffic). Also, enabling MitM without installing or trusting the cert will cause failures.
Final Thoughts
- Surge’s HTTPS decryption makes it convenient to inspect local or LAN device traffic. With it, features like custom ad blocking become feasible.
- Note that Surge cannot fully replace Charles or Fiddler; it covers basic packet capture use cases.

