title: “Disable Annoying WeChat URL Interception” tags:
- 网络工具
- 通信工具 slug: f92e81c3 date: 2022-02-27 21:54:06 summary: “Fix WeChat’s URL interception prompt using a Tampermonkey userscript and other techniques to streamline page opening.”
When opening certain pages in WeChat, you often see the interception warning below and must click “Continue to visit”. As a tech person, I can’t stand this kind of interruption, so I set out to fix the experience with a technical approach.
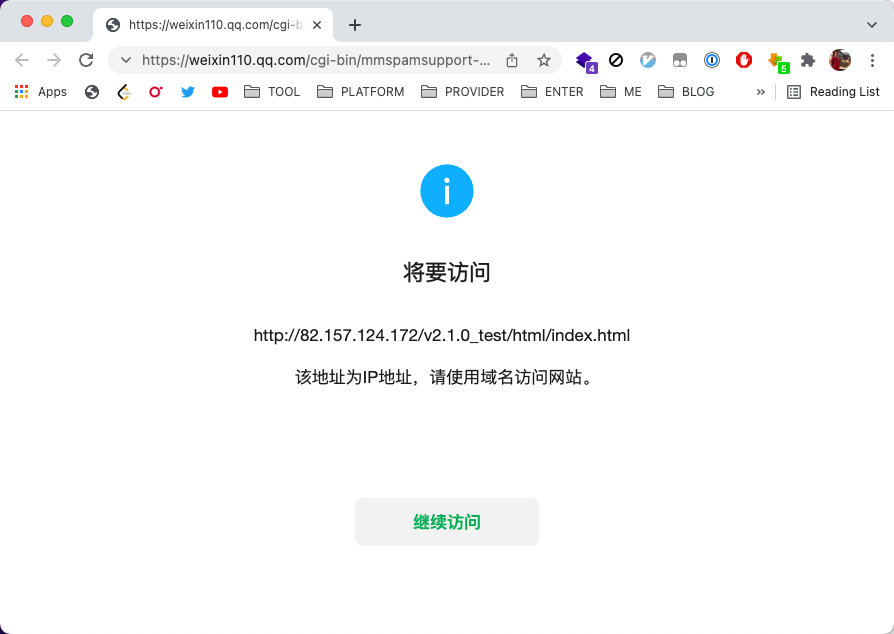
Tampermonkey Browser Extension
This was my first idea. Steps:
Install Tampermonkey in Chrome.
Add the following script in the extension. I’ve open-sourced it — if you don’t care about the details, just install it.
// ==UserScript== // @name Redirect URL // @namespace https://1991421.cn // @version 0.1 // @description 解决恼人的网页拦截,比如微信打开链接 // @author Alan He // @match https://weixin110.qq.com/cgi-bin/mmspamsupport-bin/newredirectconfirmcgi* // @icon data:image/gif;base64,R0lGODlhAQABAAAAACH5BAEKAAEALAAAAAABAAEAAAICTAEAOw== // @grant none // @run-at document-end // ==/UserScript== (function() { 'use strict'; function htmlDecode(input) { var doc = new DOMParser().parseFromString(input, 'text/html'); return doc.documentElement.textContent; } if(window.location.href.match(/^https:\/\/weixin110.qq.com\/cgi-bin\/mmspamsupport-bin\/newredirectconfirmcgi/)){ window.location.href=htmlDecode(cgiData.url); } })();
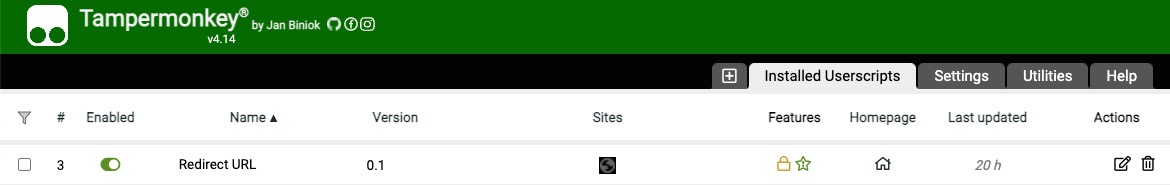
After this, when a page is intercepted, it will quickly redirect to the target site.
This works because:
- The Chrome extension can execute scripts in the page context.
- Inspecting the WeChat interception page shows there’s a
cgiDataobject in the JS context, andcgiData.urlholds the destination. Once the page reaches DCL, the script redirects to that URL.
The problem is technically solved, but there’s a drawback: the redirect happens after the page loads, so the user can still perceive the jump.
If we want to push the experience further 🚀, is there a better approach? YES!
MiTM (Man‑in‑the‑Middle) via Browser Proxy
The prior approach runs after the page fully loads. With a proxy, we can parse the WeChat response HTML before it reaches the browser, extract cgiData.url, and craft a redirect response with Location: cgiData.url. Problem solved.
Note that the interception page is HTTPS. To parse it, the proxy must support MiTM; otherwise you only see the domain, not the parameters.
With the approach clear, implementation remains.
There are many proxy apps (Charles/Surge/Whistle). I use Surge most often, so I’ll use Surge here.
Enable system proxy so Chrome routes through it.
Enable MiTM and add the
weixin110.qq.comdomain. To verify, visit the interception page and check that the certificate is issued by Surge.Add a module with a script to perform the redirect. I’ve open-sourced it — just install it if you don’t need the details.
跳转脚本如下:
/**
* 获取微信拦截网页中目标网页地址,直接返回重定向
*/
(function redirectUrl() {
try {
let cgiData = $response.body.match(/(?="url":").+(?=","btns)/)[0];
cgiData = cgiData.substring(7).replace(new RegExp('/', 'g'), '/');
$done({
headers: {
Location: cgiData
},
status: 301
});
} catch (e) {
$done({});
}
})();
After this, clicking a link in WeChat takes you directly to the destination — a noticeably better experience.
This works because:
- The proxy app ensures requests/responses pass through it so it can process them.
- MiTM enables HTTPS parsing.
- The proxy app can read/modify request and response data.
Compared to the first approach, this one clearly feels better, though it comes with a higher setup cost since you need to configure the proxy app.
Also note: MiTM doesn’t always work. If a site tightens security with HPKP/Certificate Pinning, MiTM may fail. For example, the Apple App Store’s search service fails when MiTM is enabled. Luckily most sites don’t enable this, including WeChat’s interception service here.
HPKP
Due to various reasons, browsers have dropped support for HPKP. You’ll see it more in non-web service contexts.
For example, in nginx you could configure it like this:
add_header Public-Key-Pins 'pin-sha256="YLh1dUR9y6Kja30RrAn7JKnbQG/uEtLMkBgFF2Fuihg="; pin-sha256="klO23nT2ehFDXCfx3eHTDRESMz3asj1muO+4aIdjiuY="; max-age=2592000; includeSubDomains';
For full details, see here.
Final Thoughts
Done.

